APTs: Tactics, Techniques, and Procedures
Advanced Persistent Threats (APTs) are among the most sophisticated and dangerous threats in the cybersecurity landscape...
Advanced Persistent Threats (APTs) are among the most sophisticated and dangerous threats in the cybersecurity landscape. These adversaries are typically highly skilled, well-funded, and often backed by nation-states or criminal organizations. Their objective is to gain persistent, long-term access to a targeted network or system, with the intent of espionage, data theft, sabotage, or intellectual property theft.
Understanding APTs: What Sets Them Apart?
APTs differ from common cybercriminals in several critical ways:
- Sophistication: APTs use highly advanced and customized malware, zero-day exploits, and other attack vectors that often evade traditional security defenses.
- Persistence: Unlike other types of attacks, APTs aim to establish a long-term foothold within a network. Attackers will often use multiple stages and layers of defense evasion to maintain access over extended periods.
- Targeted Attacks: APTs focus on specific high-value targets, such as governments, critical infrastructure, financial institutions, or multinational corporations. Their attacks are often tailored to the victim’s environment.
- Stealth: APTs are known for their ability to operate undetected for long periods. They often use low-and-slow techniques, making detection difficult for traditional security monitoring solutions.
- Resource-Intensive: APTs often have significant backing in terms of funding, knowledge, and resources, making them capable of launching prolonged and resource-intensive campaigns.
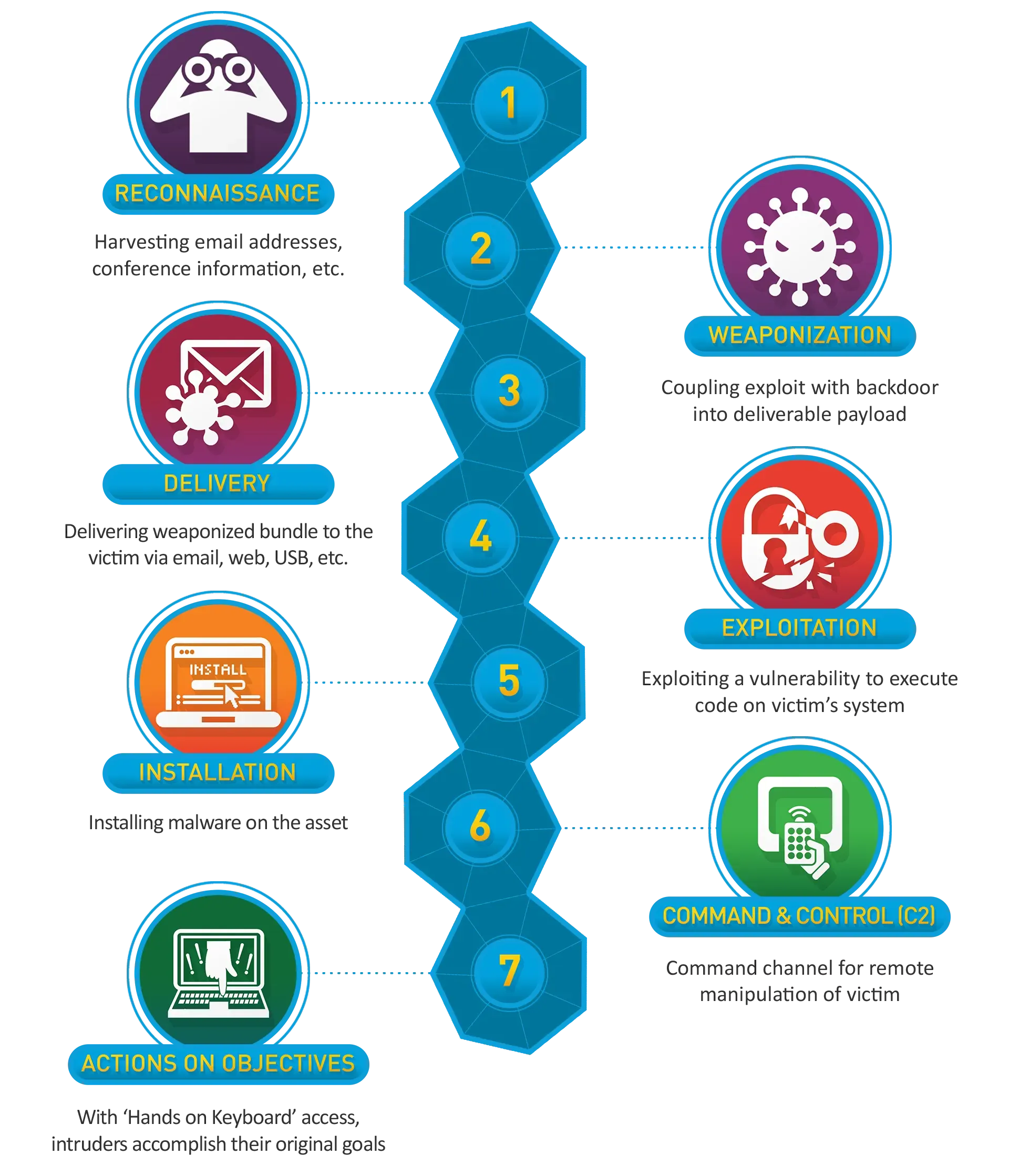
To fully understand APTs, it’s important to break down their TTPs and analyze how they operate through the cyber kill chain.
Do you like this content and want to stay updated with the latest articles, tutorials, and insights on cybersecurity? Sign up for our newsletter to receive regular updates directly in your inbox!
We respect your privacy and will never share your information with third parties.
Subscribe to NewsletterAPT Tactics, Techniques, and Procedures (TTPs)
The tactics, techniques, and procedures employed by APTs are diverse and often evolve based on the specific objectives of an attack. The MITRE ATT&CK framework provides a comprehensive matrix for classifying the techniques used by APTs, mapping them against different stages of the attack lifecycle. Let’s examine some of the most common TTPs used by APT groups.
1. Initial Access
The first stage of an APT attack is gaining an initial foothold in the target network. This can be achieved through various methods, such as:
- Spear phishing: APT actors often craft highly targeted spear phishing emails that are customized for the victim. These emails may contain malicious attachments, such as macro-laden documents, or include links to websites hosting exploit kits.
- Exploiting vulnerabilities: APT groups commonly target unpatched vulnerabilities in publicly exposed services, web applications, or remote desktop services. Zero-day vulnerabilities are particularly valuable because they are unknown to security vendors.
- Supply chain attacks: By compromising a trusted third-party vendor or software provider, APTs can infiltrate target organizations by piggybacking on legitimate software updates or services.
2. Execution
Once initial access is gained, the next stage involves executing malicious payloads or commands on the target system.
- Remote Code Execution (RCE): Exploiting remote vulnerabilities allows attackers to execute code remotely on the victim’s machine.
- Scripting and command-line interfaces: APT actors often use built-in tools such as PowerShell, Windows Management Instrumentation (WMI), or bash scripting to avoid detection by executing commands in-memory, rather than writing them to disk.
- Custom malware: APTs frequently deploy customized malware payloads designed to bypass traditional antivirus and endpoint protection measures.
3. Persistence
Maintaining long-term access to the target system is one of the key objectives for APTs. To achieve this, they employ several persistence techniques:
- Credential theft: Using tools like Mimikatz, attackers can extract credentials from memory or Active Directory to maintain access to the network, even if the initial attack vector is closed.
- Backdoors and implants: APTs deploy backdoors and implants that give them remote access to the compromised network, enabling them to re-enter the environment even if detected and removed.
- Registry keys and scheduled tasks: Modifying registry keys or setting up scheduled tasks allows attackers to persist on the system, ensuring that their malware is re-executed even after a system reboot.
4. Privilege Escalation
To move laterally and access high-value systems within the target network, APTs often escalate privileges using techniques such as:
- Exploiting vulnerabilities in system services: Attackers look for privilege escalation vulnerabilities within operating systems or applications to gain higher-level permissions.
- Token manipulation and SID history injection: These techniques allow attackers to impersonate other users, including administrative accounts, to gain access to sensitive systems.
5. Defense Evasion
APTs are adept at avoiding detection and evading security defenses, employing various techniques, including:
- Living off the land: Rather than deploying external tools, APTs often leverage legitimate tools and processes, such as system administration utilities or native scripting environments, to evade detection.
- Fileless attacks: By executing code in-memory or within existing processes, APTs can bypass endpoint detection and response (EDR) systems that rely on disk-based signatures.
- Obfuscation and encryption: Malware and communications between compromised systems and the command-and-control (C2) servers are often heavily obfuscated or encrypted to prevent analysis and detection by security tools.
6. Lateral Movement
Once inside the target network, APTs move laterally to other systems and networks to gather more information or access more sensitive areas:
- Remote Desktop Protocol (RDP): APT actors may use RDP to move laterally between systems.
- Pass-the-Hash (PtH) and Pass-the-Ticket (PtT): By stealing and reusing authentication tokens, such as hashed credentials or Kerberos tickets, attackers can move between systems without needing to compromise each one individually.
7. Exfiltration
After successfully navigating the victim’s network, the final stage involves exfiltrating sensitive data:
- Data staging and compression: Large amounts of data are often compressed and staged in a location accessible to the attackers for future extraction.
- Steganography: Some APTs use steganography to hide data within images, videos, or other file types to evade detection during exfiltration.
- Encrypted tunnels: Attackers often use encrypted tunnels or VPNs to transfer stolen data out of the network to avoid detection by network security monitoring tools.
Real-World Case Studies: Prominent APT Groups and Their Attacks
To better understand the methodology and impact of APT attacks, let’s examine some real-world case studies involving well-known APT groups.
APT29 (Cozy Bear)
APT29, also known as Cozy Bear, is believed to be associated with Russian intelligence agencies. This group is known for its stealthy and sophisticated attacks, focusing on espionage against Western governments and organizations.
- Operation Cloud Hopper: APT29’s most notable operation involved a multi-year espionage campaign targeting managed service providers (MSPs) to access the networks of their clients. The attackers gained access to sensitive government and corporate data by compromising the supply chain, exploiting vulnerable software, and using advanced obfuscation techniques to evade detection.
APT41 (Winnti Group)
APT41, also known as Winnti Group, is a Chinese APT that is unique in its blend of state-sponsored espionage and financially motivated cybercrime. APT41 has been linked to various campaigns targeting sectors such as healthcare, telecommunications, and software development.
- Operation ShadowPad: In this operation, APT41 compromised widely used software platforms by embedding backdoors into legitimate software updates. One of their most high-profile targets was NetSarang, a company that provides network management software used by major enterprises. Through the infected software updates, APT41 gained access to multiple organizations, including healthcare providers and financial institutions.
APT10 (Stone Panda)
APT10, also known as Stone Panda, is another Chinese state-sponsored group known for conducting cyber espionage campaigns, particularly against technology companies and government agencies.
- Cloud Hopper Campaign: This operation targeted cloud service providers and their customers, giving APT10 access to sensitive corporate data across multiple industries. The attackers leveraged spear phishing and exploited vulnerabilities in VPN software to infiltrate cloud infrastructure and compromise client networks.
Conclusion: The Evolving Threat of APTs
Advanced Persistent Threats are some of the most dangerous adversaries that organizations face today. Their sophisticated, multi-stage attacks are carefully crafted to evade detection and remain in target networks for extended periods. Understanding the TTPs employed by APTs is critical to building effective defenses and improving incident response capabilities.
Related Posts




